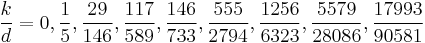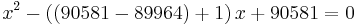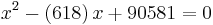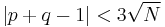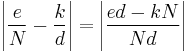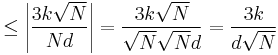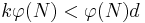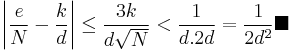Wiener's Attack
The public-key cryptosystem RSA is frequently used for security applications such as email, credit card payments, login network access, etc. The security of RSA depends on the choice of certain parameters. Wiener's attack uses the continued fraction method to exploit a mistake made in the use of RSA. This error could be exploited when users are doing transactions using credit card or mobile devices such as phones.
Contents |
Introduction
Before we discuss how Wiener's attack works, we will first briefly explain how RSA works. For more details see the main entry on the RSA cryptosystem. Let Alice and Bob be two people who want to communicate securely. More specifically, Alice wants to send a message to Bob which only Bob can read. First Bob chooses two primes p and q. Then he calculates the RSA modulus N = pq. This RSA modulus is made public together with the encryption exponent e, N and e form the public key pair (e,N). By making this information public, anyone can encrypt messages to Bob. The decryption exponent d satisfies  , where
, where 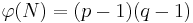 , is Euler’s phi function (note: this is the order of the multiplicative group
, is Euler’s phi function (note: this is the order of the multiplicative group  ). The encryption exponent e and
). The encryption exponent e and  also must be relatively prime so that there is a modular inverse. The factorization of N and the private key d are kept secret, so that only Bob can decrypt the message. We denote the private key pair as (d, N). The encryption of the message M is given by
also must be relatively prime so that there is a modular inverse. The factorization of N and the private key d are kept secret, so that only Bob can decrypt the message. We denote the private key pair as (d, N). The encryption of the message M is given by 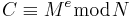 and the decryption of cipher text
and the decryption of cipher text 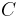 is given by
is given by 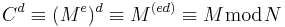 (using Fermat's little theorem).
(using Fermat's little theorem).
Using the Euclidean algorithm, one can efficiently recover the secret key d if one knows the factorization of N. By having the secret key d, one can efficiently factor the modulus of N.[1]
In the RSA Cryptosystem, Bob might tend to use a small value of d, rather than a large random number to improve the RSA decryption performance. However, Wiener’s attack shows that choosing a small value for d will result an insecure system in which an attacker can recover all secret information, i.e., break the RSA system. This break is based on Wiener’s Theorem, which holds for small values of d. Wiener has proved that the attacker may efficiently find d when 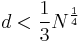 .[2]
.[2]
Wiener's paper also presented some countermeasures against his attack that allow fast decryption. Two techniques are described as follows.
Choosing large public key: Replace 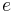 by
by 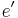 , where
, where 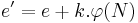 for some large of
for some large of 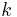 . When
. When 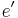 is large enough, i.e.
is large enough, i.e. 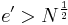 , then Wiener’s attack can not be applied regardless of how small
, then Wiener’s attack can not be applied regardless of how small 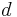 is.
is.
Using the Chinese Remainder Theorem: Suppose one chooses d such that both 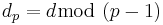 and
and 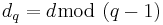 are small but
are small but 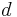 itself is not, then a fast decryption of
itself is not, then a fast decryption of 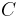 can be done as follows:
can be done as follows:
1. First compute 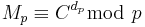 and
and 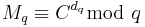 .
.
2. Use the Chinese Remainder Theorem to compute the unique value of 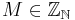 which satisfies
which satisfies 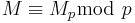 and
and 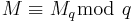 . The result of
. The result of 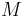 satisfies
satisfies 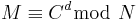 as needed. The point is that Wiener’s attack does not apply here because the value of
as needed. The point is that Wiener’s attack does not apply here because the value of 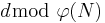 can be large. [3]
can be large. [3]
How Wiener's Attack Works
Since
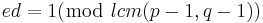 ,
,
there exists an integer K such that
Define 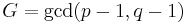 to be substituted in the equation above which gives:
to be substituted in the equation above which gives:
Defining  and
and 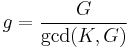 , and substituting into the above gives:
, and substituting into the above gives:
 .
.
Divided by 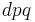 :
:
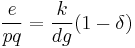 , where
, where 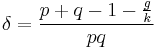 .
.
So, 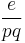 is slightly smaller than
is slightly smaller than 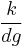 , and the latter is composed entirely of public information. However, a method of checking a guess is still required. Assuming that
, and the latter is composed entirely of public information. However, a method of checking a guess is still required. Assuming that 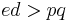 (a reasonable assumption unless
(a reasonable assumption unless  is large) the last equation above may be written as:
is large) the last equation above may be written as:
By using simple algebraic manipulations and identities, a guess can be checked for accuracy. [1]
Theorem (M. Wiener)
Let 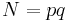 with
with 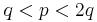 . Let
. Let 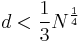 .
.
Given 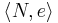 with
with  , the attacker can efficiently recover
, the attacker can efficiently recover 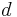 .[2]
.[2]
Example
Suppose that the public keys are 
The attack shall determine 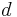 .
.
By using Wiener's Theorem and continued fractions to approximate 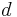 , first we try to find the continued fractions expansion of
, first we try to find the continued fractions expansion of 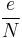 . Note that this algorithm finds fractions in their lowest terms. We know that
. Note that this algorithm finds fractions in their lowest terms. We know that
According to the continued fractions expansion of 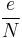 , all convergents
, all convergents  are:
are:
We can verify that the first convergent does not produce a factorization of 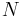 . However, the convergent
. However, the convergent 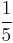 yields
yields
Now, if we solve the equation
then we find the roots which are  . Therefore we have found the factorization
. Therefore we have found the factorization
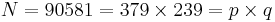 .
.
Notice that, for the modulus 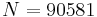 , Wiener's Theorem will work if
, Wiener's Theorem will work if
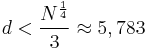 .
.
Proof of Wiener's Theorem
The proof is based on approximations using continued fractions.[2][4]
Since  , there exists a
, there exists a 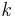 such that
such that  . Therefore
. Therefore
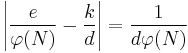 .
.
Hence,  is an approximation of
is an approximation of 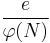 . Although the attacker does not know
. Although the attacker does not know  , he may use
, he may use 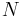 to approximate it. Indeed, since
to approximate it. Indeed, since
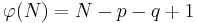 and
and  , we have:
, we have:
Using 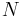 in place of
in place of  we obtain:
we obtain:
Now, 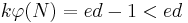 , so
, so 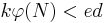 . Since
. Since 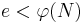 , so
, so 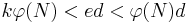 , then we obtain:
, then we obtain:
Since 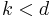 and
and 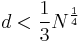 . Hence we obtain:
. Hence we obtain:
- (1)

Since 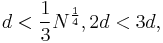 then
then  , we obtain:
, we obtain:
 , so (2)
, so (2) 
From (1) and (2), we can conclude that
References
- ^ a b L. Render, Elaine (2007). Wiener's Attack on Short Secret Exponents.
- ^ a b c Boneh, Dan (1999). Twenty Years of attacks on the RSA Cryptosystem. Notices of the American Mathematical Society (AMS) 46 (2).
- ^ Cui, Xiao-lei (2005). Attack On the RSA Cryptosystem.
- ^ Khaled Salah, Imad (2006). Mathematical Attacks on RSA Cryptosystem. Journal of Computer Science 2 (8)). pp. 665-671.
Further reading
- Coppersmith, Don (1996). Low-Exponent RSA with Related Messages. Springer-Verlag Berlin Heidelberg.
- Jose, Justin (2010). Study of RSA and Proposed Variant Against Wiener's Attack. International Journal of Computer Applications.
- Dujella, Andrej (2004). Continued Fractions and RSA with Small Secret Exponent.
- R. Stinson, Douglas (2002). Cryptography Theory and Practice (2e ed.). A CRC Press Company. pp. 200–204. ISBN 1-58488-206-9.



![\frac{e}{N} = \frac{17993}{90581} = \cfrac{1}{5 %2B \cfrac{1}{29 %2B\dots %2B \cfrac{1}{3}}} = \left [0,5,29,4,1,3,2,4,3 \right ]](/2012-wikipedia_en_all_nopic_01_2012/I/a784de835ebfa628388b15d7c8a89a0c.png)